Raymii.org

אֶשָּׂא עֵינַי אֶל־הֶהָרִים מֵאַיִן יָבֹא עֶזְרִֽי׃Home | About | All pages | Cluster Status | RSS Feed
Self Hosted CryptoCat - Secure self hosted multiuser webchat
Published: 09-11-2013 | Author: Remy van Elst | Text only version of this article
❗ This post is over twelve years old. It may no longer be up to date. Opinions may have changed.
Table of Contents
This is a guide on setting up a self hosted secure multiuser webchat service with CryptoCat. It covers the set up of ejabberd, nginx and the web interface for CryptoCat. It supports secure encrypted group chat, secure encrypted private chat and file and photo sharing.
This tutorial is tested on Ubuntu 12.04.
If you want to set up a federated XMPP Chat Network with ejabberd, see my tutorial how to do that.
Set up a DNS record
Make sure you set up two DNS A records to your chat server. One should be for
example chat.sparklingclouds.nl and the other is for the conferencing:
conference.chat.sparklingclouds.nl. You should contact your provider if you
need help with this.
In the configuration files, you should replacechat.sparklingclouds.nl with
your own domain name.
Install required packages
First we install the required packages:
apt-get install ejabberd nginx vim git
ejabberd configuration
Edit the ejabberd configuratio file located:
/etc/ejabberd/ejabberd.cfg
And place the following contents in it, replacing chat.sparklingclouds.nl with your own domain:
%% Hostname
{hosts, ["chat.sparklingclouds.nl"]}.
%% Logging
{loglevel, 0}.
{listen,
[
{5222, ejabberd_c2s, [
{access, c2s},
{shaper, c2s_shaper},
{max_stanza_size, infinite},
%%zlib,
starttls, {certfile, "/etc/ejabberd/ejabberd.pem"}
]},
{5280, ejabberd_http, [
http_bind,
http_poll
]}
]}.
{s2s_use_starttls, true}.
{s2s_certfile, "/etc/ejabberd/ejabberd.pem"}.
{auth_method, internal}.
{auth_password_format, scram}.
{shaper, normal, {maxrate, 500000000}}.
{shaper, fast, {maxrate, 500000000}}.
{acl, local, {user_regexp, ""}}.
{access, max_user_sessions, [{10, all}]}.
{access, max_user_offline_messages, [{5000, admin}, {100, all}]}.
{access, c2s, [{deny, blocked},
{allow, all}]}.
{access, c2s_shaper, [{none, admin},
{normal, all}]}.
{access, s2s_shaper, [{fast, all}]}.
{access, announce, [{allow, admin}]}.
{access, configure, [{allow, admin}]}.
{access, muc_admin, [{allow, admin}]}.
{access, muc, [{allow, all}]}.
{access, register, [{allow, all}]}.
{registration_timeout, infinity}.
{language, "en"}.
{modules,
[
{mod_privacy, []},
{mod_ping, []},
{mod_private, []},
{mod_http_bind, []},
{mod_admin_extra, []},
{mod_muc, [
{host, "conference.@HOST@"},
{access, muc},
{access_create, muc},
{access_persistent, muc},
{access_admin, muc_admin},
{max_users, 500},
{default_room_options, [
{allow_change_subj, false},
{allow_private_messages, true},
{allow_query_users, true},
{allow_user_invites, false},
{anonymous, true},
{logging, false},
{members_by_default, false},
{members_only, false},
{moderated, false},
{password_protected, false},
{persistent, false},
{public, false},
{public_list, true}
]}
]},
{mod_register, [
{welcome_message, {"Welcome!"}},
{access, register}
]}
]}.
If you want a signed ejabberd ssl certificate you can read my tutorial how to do that
NGINX Configuration
We need an SSL certificate for the web server. You can generate one yourself using the following command:
cd /etc/ssl/certs
openssl req -nodes -x509 -newkey rsa:4096 -keyout key.pem -out cert.crt -days 356
Or generate a CSR and let it sign by a "official" CA like verisign or digicert:
cd /etc/ssl/certs
openssl req -nodes -newkey rsa:4096 -keyout private.key -out CSR.csr
When the certificate is in place you can continue to configure NGINX.
Edit the file or create a new virtual host.
vim /etc/nginx/sites-enabled/default
And place the following contents in it, replacing chat.sparklingclouds.nl with your own domain:
server {
listen 80;
listen [::]:80 default ipv6only=on;
server_name chat.sparklingclouds.nl;
rewrite ^ https://$server_name$request_uri? permanent;
add_header Strict-Transport-Security max-age=31536000;
location / {
root /var/www;
index index.html index.htm;
}
}
# HTTPS server
server {
listen 443;
server_name chat.sparklingclouds.nl;
add_header Strict-Transport-Security max-age=31536000;
ssl on;
ssl_certificate /etc/ssl/certs/cert.crt;
ssl_certificate_key /etc/ssl/certs/key.pem;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 5m;
ssl_protocols TLSv1.1 TLSv1.2;
ssl_ciphers ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-RC4-SHA:ECDHE-RSA-AES128-SHA:RC4:HIGH:!MD5:!aNULL:!EDH;
ssl_prefer_server_ciphers on;
location / {
root /var/www;
index index.html index.htm;
}
location /http-bind {
proxy_buffering off;
tcp_nodelay on;
keepalive_timeout 55;
proxy_pass http://127.0.0.1:5280/http-bind;
}
}
Save it and restart NGINX:
/etc/init.d/nginx restart
Cronjob for ejabberd
This is important, it cleans up unused ejabberd accounts. Create a new crontab like so:
crontab -e
And place the following in it:
1 1 * * * ejabberdctl delete-old-users 1
That way once every 24 hours the ejabberd server gets cleaned up.
Web Frontend
Note that you now already can use your own server with the CryptoCat frontend via: https://crypto.cat. We are going to set up our own frontend on our webserver so we don't need Crypto.Cat.
Setting up a web frontend is not recommended by the cryptocat developers. See the comment below, and read the full thread on this Reddit post
When you host Cryptocat as a website, this means that every time someone wants to use it, they technically will need to re-download the entire code by visiting the website. This means that every use needs a full re-download of the Cryptocat code. By centralizing the code redistribution in a "web front-end" and making it necessary for everyone to redownload the code every time, you create an opportunity for malicious code poisoning by the host, or code injection by a third party. This is why the only recommended Cryptocat download is the browser extension from the official website, which downloads only once as opposed to every time (just like a regular desktop application), and is authenticated by Cryptocat's development team as genuine.
Kaepora - 12-11-2013 on Reddit
Take that into consideration when setting up the frontend. A use case could be an internal cryptocat chat service where people don't need to change the default server address and such.
First get the source code:
cd /tmp
git clone https://github.com/cryptocat/cryptocat.git
Then place it in the right folder;
cp -r cryptocat/src/core /var/www/
Edit the config file to use your own server:
cd /var/www
vim js/cryptocat.js
And place the following contents in it, replacing chat.sparklingclouds.nl with your own domain:
/* Configuration */
// Domain name to connect to for XMPP.
var defaultDomain = 'chat.sparklingclouds.nl'
// Address of the XMPP MUC server.
var defaultConferenceServer = 'conference.chat.sparklingclouds.nl'
// BOSH is served over an HTTPS proxy for better security and availability.
var defaultBOSH = 'https://chat.sparklingclouds.nl/http-bind/'
Now save the file.
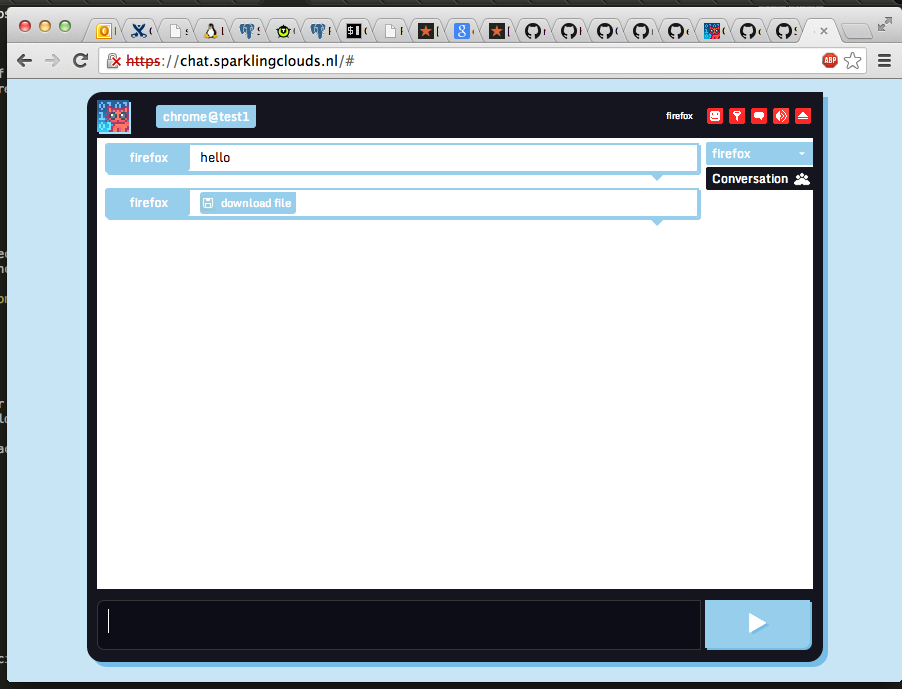
You are finished now. Go to your website and test the chat out.
Tags: chat , cryptocat , ejabberd , jabber , nginx , tutorials , xmpp