Raymii.org

אֶשָּׂא עֵינַי אֶל־הֶהָרִים מֵאַיִן יָבֹא עֶזְרִֽי׃Home | About | All pages | Cluster Status | RSS Feed
Gitlab Active Directory LDAP Authentication
Published: 28-05-2013 | Author: Remy van Elst | Text only version of this article
❗ This post is over twelve years old. It may no longer be up to date. Opinions may have changed.
Gitlab is a self hosted git based source control application similar to Github, written in Ruby on Rails. It is used by many organisations and is a wonderfull piece of software. It supports LDAP Authentication (via the OmniAuth Gem), but it is tricky to set up with Active Directory and Windows Server 2003/2008/2012. This tutorials shows you how to set up Gitlab to authenticate against Active Directory LDAP.
You have to have a working Gitlab installation for this. It is tested with Gitlab 3 and up to 5.2, with an Active Directory 2008 env, and a Mixed 2008 & 2003 AD. Gitlab is installed on a Ubuntu box.
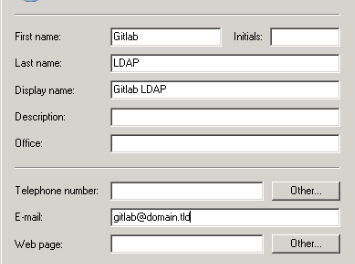
First create a user in the Active Directory. My CN is Users, and my user is
named gitlab. It does not have any special permissions, it is just a normal
user. Note the Full Name you use, in my example it is "Gitlab LDAP". See the
image below for an example:
Now go to your Gitlab server, log in and become the git user:
sudo su - git
And edit the ~/gitlab/config/gitlab.yml file. (Assuming you followed the
official installation guide, otherwise adapt path.). The relevant LDAP section
should contain this:
ldap:
enabled: true
host: 'pdc1.domain.tld'
base: 'CN=Users,DC=Domain,DC=tld'
port: 389
uid: 'sAMAccountName'
method: 'plain' # or "ssl"
bind_dn: 'CN=Gitlab LDAP,CN=Users,DC=Domain,DC=tld'
password: 'example_password'
It took me a while to find the correct bind_dn and base_dn. It appears that
they are capital sensitive, cn=Users would not work, but CN=Users does.
Also, the bind_dn does not use the users email address, but the Display
Name. So CN=gitlab@domain.tld does not work, but CN=Gitlab LDAP does.
Hope this helps you setting up Gitlab with LDAP auth. More info on Gitlab can be found on their website: http://gitlab.org/.
Tags: active-directory , git , github , gitlab , gitlabshell , ldap , microsoft , scm , source-control , tutorials , windows-server